
| HOME | TRAINING | SERVICES | BLOG | COMPUTER TIPS | NEWS | CONTACT US |
WIRELESS NETWORKING
Wireless Network Modes
The simplest wireless network consists of two or more PCs communicating
directly with each other sans cabling or any other intermediary hardware.
More complicated wireless networks use a WAP to centralize wireless
communication and bridge wireless network segments to wired network
segments. These two different methods are called ad-hoc mode and infrastructure
mode.
 wireless NIC
wireless NIC  wireless access point
wireless access point
Ad-hoc Mode
Ad-Hoc mode is sometimes called peer to peer mode, which each wireless
node in direct contact with each other node in a decentralized free for all. This is suited for
wireless networks use in small groups also known as Independent basic Service Set (IBSS)
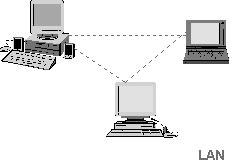 Ad Hoc Mode
Ad Hoc Mode
Infrastructure Mode
Wireless networks running in infrastructure mode use one or more WAPs
to connect the wireless network nodes to a wired network segment,
as shown above. A single WAP servicing a given area is called a Basic
Service Set (BSS). This service area can be extended by adding more
WAPs. This is called, appropriately, an Extended basic Service Set
(EBSS).
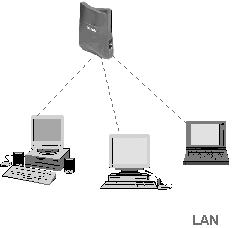 Infrastructure
Mode
Infrastructure
Mode
Wireless
Networking Security
One of the major complaints against wireless networking is that it
offers weak security. In many cases, the only thing you need to do
to access a wireless network is walk into a WAP’s coverage area
and turn on your wireless device! Further, data packets are floating
through the air instead of safely wrapped up inside network cabling.
What’s to stop an unscrupulous PC tech with the right equipment
from grabbing those packets out of the air and reading that data himself?
Wireless networks use three methods to secure access to the network
itself and secure the data that’s’ being transferred.
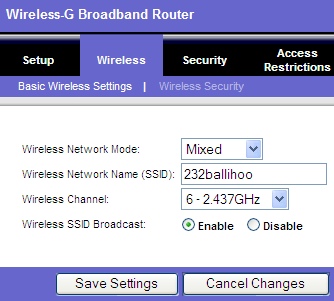
The SSID (network name) parameter ensures that only wireless network
devices configured with the same SSID are permitted access to the
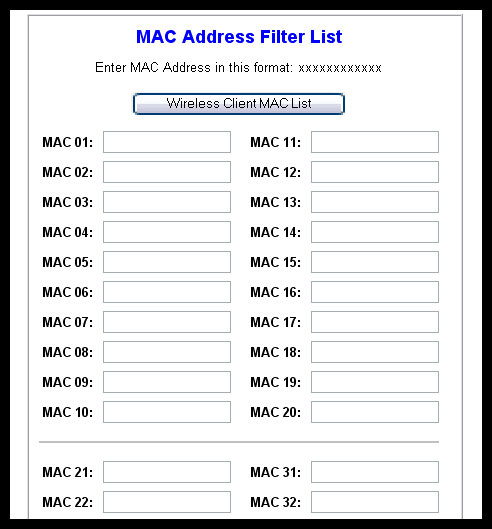
network. You can tighten security even further by employing MAC filtering,
a way of creating a list of machines that are permitted to access
the network. Enabling wireless encryption through either Wireless
Equivalency Privacy (WEP) or Wi-Fi Protected Access (WPA) ensures
that the data packets themselves are secure while in transit
Wireless Networking Security (War Chalking, War Driving and Hot Spots)
Wireless Antennas (Omni Directional vs. Yagi Directional Antennas)
Wireless Channels (mostly use 1, 6 and 11) for 2.4Ghz
Wireless Channels (23 channels) for5Ghz
SSID
The service set identification (SSID), sometimes called a network
name, is a 32bit identification string that's inserted into the header
of each data packet processed by a wireless access point. This provides
the basic unit of wireless security.
MAC
Filtering
MAC filtering, a method that enables you to limit access
to your wireless network based on the physical, hard wired addresses
of the wireless network adapters you support
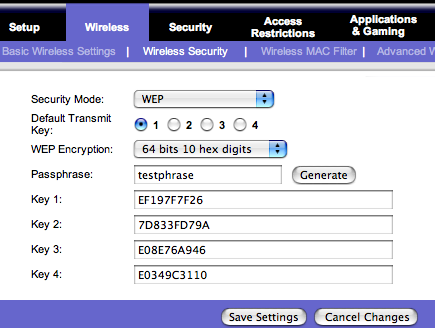
WEP
Wireless Equivalency Privacy (WEP) uses a 64bit-128bit encryption
algorithm to scramble data packets as sent in a wireless transmission
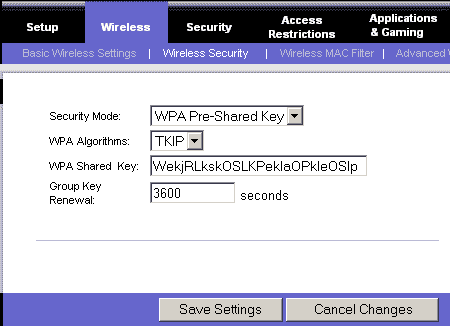
WPA
WPA addresses the weaknesses of WEP, and acts as a sort of security
protocol upgrade to WEP-enabled devices. WPA offers security enhancement
such as an encryption key integrity-checking feature and user authentication
through the industry-standard Extensible Authentication Protocol (EAP).
The use of EAP is a huge security improvement over WEP’s MAC
address authentication scheme. After all, MAC addresses are fairly
easy to “sniff” out, since they’re transmitted in
unencrypted, clear-text format. User names and passwords are encrypted,
and therefore much more secure.
Even with these enhancements, WPA is only intended as an interim security
solution until the IEEE 802.11i security standard is finalized and
implemented.
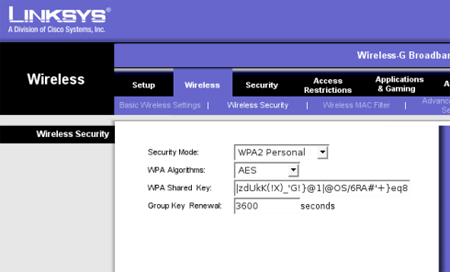
WPA2
WPA2 supports the IEEE 802.11ac standard which also offers AES advance encryption system
support
WPA3
WPA3 supports the IEEE 802.11ac and ax standard which also offers AES advance encryption system
support
EAP – Extensible Authentication Protocol is an authentication framework used inwireless networks and point to point connections.
Types of EAP
LEAP, TLS, MD5, PSK, TTLS, IKEv2, FAST, SIM, AKA, GTC and EKE
Encapsulation – IEEE 802.1x, PEAP, RADIUS, Diameter, PANA and PPP
Wireless
Networking Standards
To gain better understanding of wireless network technology, let’s
take a brief look at the standards they use.
IEEE
802.11-Based Wireless Networking
The IEEE 802.11 wireless Ethernet standard defines methods by which
devices may communicate using spread-spectrum radio waves. Spread-spectrum
broadcast data in small, discrete chunks over different frequencies
available within a certain frequency range. All of the 802.11-based
wireless technologies broadcast and receive at 2.4 GHz (with the exception
of 802.11a, which uses 5 GHz). The original 802.11 standard has been
extended to 802.11a, 802.11b, and 802.11g variations used in Wi-Fi
wireless networks, and also hybridized (combined with another wireless
communication technology) to form the Shared Wireless Access Protocol
(SWAP) used in Home RF networks.
Spread-Spectrum
Broadcasting
Spread spectrum refers to the manner in which data signals travel through a radio frequency. The 2 types of spread spectrum are direct-sequence spread-spectrum (DSSS) and frequency-hopping spread-spectrum (FHSS). DSSS sends data out on different frequencies at the same time, while FHSS sends data on one frequency at a time, constantly shifting (or hopping) frequencies. DSSS uses considerably more bandwidth than FHSS.
DSSS is capable of greater data throughput, but DSSS is also more prone to interference than FHSS.
(OFDM) Orthogonal Frequency Division Multiplexing is a method of encoding digital data on multiple carrier frequencies.
The
802.11 Standard
Devices that use the original 802.11 (with no letter) standard are
a rarity these days. You’re most likely to find them in service
on some brave early adopter’s network.
The original 802.11 standard was hampered by both slow speeds (2 Mbps
maximum) and limited range (about 150 feet). However, 802.11 employed
some of the same features that are in use in the current wireless
standards. 802.11 uses the same 2.4 GHz broadcast range, and security
is provided by the use of industry-standard WEP and WAP encryption.
802.11 Chart
| Standard | 802.11ac | 802.11a | 802.11b | 802.11g | 802.11n |
| Speed | 1000 up to 3200Mbps | 54Mbps | 11Mbps | 54 Mbps | 100-600Mbps |
| Range | 75ft | 150ft | 300ft | 300ft | 300ft |
| Frequency | 2.4GHz | 5GHz | 2.4GHz | 2.4GHz | 2.4-5GHz |
| Security | SSID, MAC filtering, WEP, WPA (TKIP) WPA2 (AES) | ||||
| Compatibility | 802.11 | 802.11a | 802.11b | 802.11g/b | 802.11n/g/b/a |
| Spread Spectrum method | DSSS | DSSS | DSSS | OFDM | OFDM |
| Mode | Ad Hoc or Infrastructure Mode | ||||
802.11n (MIMO) Multiple Input/Multiple Output (Found on some wireless networks today)
802.11ac the newest wireless standard which will support 1Gpbs speed
Infrared
Wireless Networking
Wireless networking using infrared technology is largely overlooked
these days, probably due to explosion of interest in the newer and
faster wireless standards. This is a shame, because infrared provides
an easy way to transfer data, often without the need to purchase or
install any additional hardware or software on your PCs.
Infrared Data Association Standard
Communication through infrared devices is enabled via the Infrared
Data Association (IrDA) protocol. The IrDA protocol stack is widely
supported industry standard, and has been included in all versions
of Windows since Windows 95.
Speed-and
range wise, infrared isn’t very impressive. Infrared devices
are capable of transferring data up to 4 Mbps. Not
too shabby, but hardly stellar. The maximum distance between
infrared devices is 1 meter.

Infrared links are direct line-of-sight, and are susceptible to interference.
Infrared devices operate at half-duplex, meaning that while one is
talking, the other is listening-they can’t talk and listen at
the same time. IrDA has a mode that emulates full-duplex communication,
but it’s really half-duplex.
Security-wise, the IrDA protocol offers exactly nothing in the way
of encryption or authentication. Infrared’s main security feature
is the fact that you have to be literally within arm’s reach
to establish a link.
Clearly, infrared is not the best solution for a dedicated network
connection, but for a quick file transfer or print job without getting
your hands dirty, it’ll do in a pinch.
| Standard | Infrared (IRDA) |
| Speed | 4Mbps |
| Range | 1 Meter |
| Security | None |
| Compatibility | Infrared Devices |
| Mode | Ad Hoc |
| Description | Infrared is best suited for quick, small transfers, such as transferring files from one PDA to another PDA and sending print jobs to an Infrared capable printer |

Bluetooth
Bluetooth wireless technology (named for 9th century Danish king Harald
Bluetooth) is designed to create small wireless Personal Area Networks
(PANs) that link PCs to peripheral devices such as PDAs and printers,
scanners, web cams, input devices like keyboards, joystick and mice,
and even consumer electronics like cell phones, head sets, home stereos,
televisions, home security systems, and so on.

Bluetooth Operation Modes
Master/Slave Scheme in which one master device can control up to seven active slave devices
Bluetooth Communication
Bluetooth devices go to four stages to find each other and start talking.
Discovery Service – Broadcast it’s MAC
address as well as what type of device it is
Name Discovery – Device identifies itself by
a friendly name such as Motorola headsets
Association – Bonding, Pairing or Joining the
device officially joins your Bluetooth network
Service Discovery – Device tells what kind
of service or profile it provides
Bluetooth services
Bluetooth
is not designed to be a full-function networking solution, nor is
it meant to compete with either Wi-Fi or HomeRF. If anything, Bluetooth
is poised to replace infrared as a means to connect PCs to peripherals.
The IEEE organization has made Bluetooth the basis for its forthcoming
802.15 standard for wireless PANs. Bluetooth uses the FHSS spread-spectrum
broadcasting method, switching between any of the 79 frequencies available
in the 2.45 GHz range. Bluetooth hops frequencies some 1,600 times
per second, making it highly resistant to interference. Some high-powered
Bluetooth devices have throughput speed of a whopping 2 Mbps and a
maximum range of up to 300 feet, but these are uncommon.
| Standard | Bluetooth |
| Speed | 1-2Mbps |
| Range | 33-300 feet |
| Frequency | 2.4GHz |
| Security | PPTP or SSL |
| Compatibility | Bluetooth Devices |
| Spread Spectrum | FHSS |
| Mode | Master and Slave (up to 7 devices) |
| Description | Popular with peripheral devices |